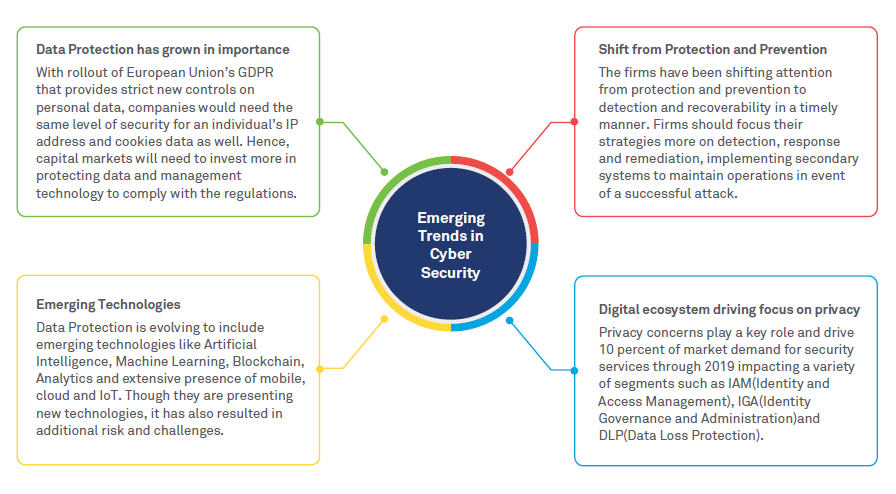
Figure 1: Emerging Cybersecurity Trends
Types of cybersecurity threats
Global companies spent up to 26 percent more for cybersecurity in 2018, as the average cost of a data breach is now up to USD 1.23 million for large companies (up 24 percent from 2017) 3 . Financial firms have the second highest cost per capita for data breaches while healthcare tops the list 4 . The frequency, sophistication and impact of cyber threats are at an all-time high. The top cybersecurity threats in 2018 5 are shown below.
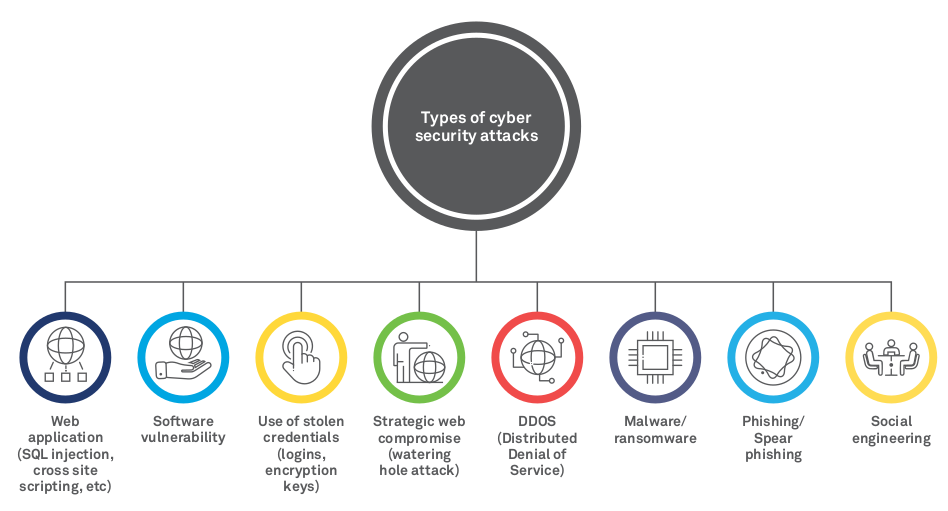
Figure 2: Types of Cybersecurity Attacks
Impact of cyber threats on capital markets
According to a study published by the International Organization of Securities Commissions (IOSCO) research department and the World Federation of Exchanges office, around half of the world’s securities exchanges were the subject of cyber attacks last year.
Cyber threats in capital markets may lead to manipulation of order management systems leading to incorrect feeds, false orders/ non-submissions, and corruption of trade surveillance systems thus enabling manipulative, illegal and abusive trade practices. All this can result in triggering automated rogue trading strategies, thereby increasing the chance of flash crashes. The cybersecurity landscape for asset and wealth management firms is also fraught with an array of threats aimed at stealing or compromising clients’ investment or personal data. With the growing adoption of wealth management applications on mobile and via cloud-based services, attacks like DDOS, ransomware and phishing are gaining popularity.
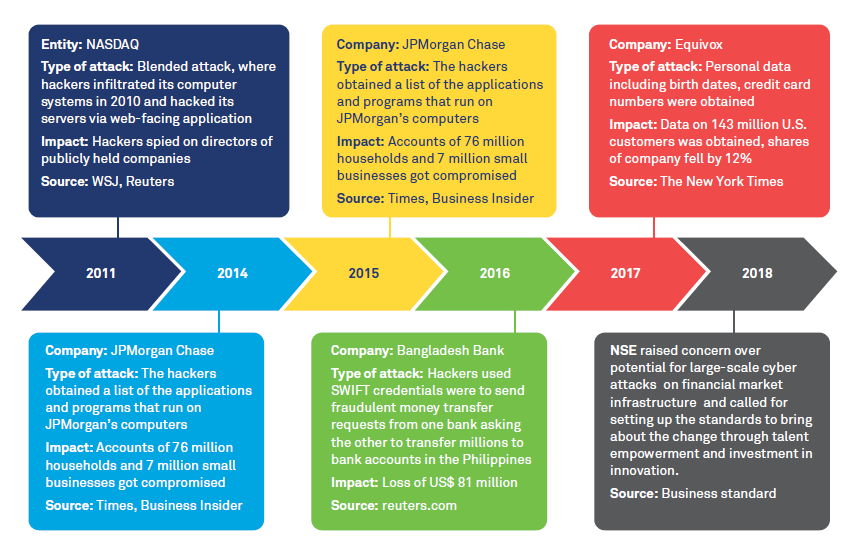
Figure 3: Top Cybersecurity Threats
Essential cybersecurity measures
Cybersecurity leaders should seek the right balance between risk, usability, resilience, and price. However, it is predicted that by 2020, more than 60% of organizations 6 will invest in multiple data security tools like data loss prevention, encryption, unified threat management, intrusion detection systems, etc., up from 35% today.
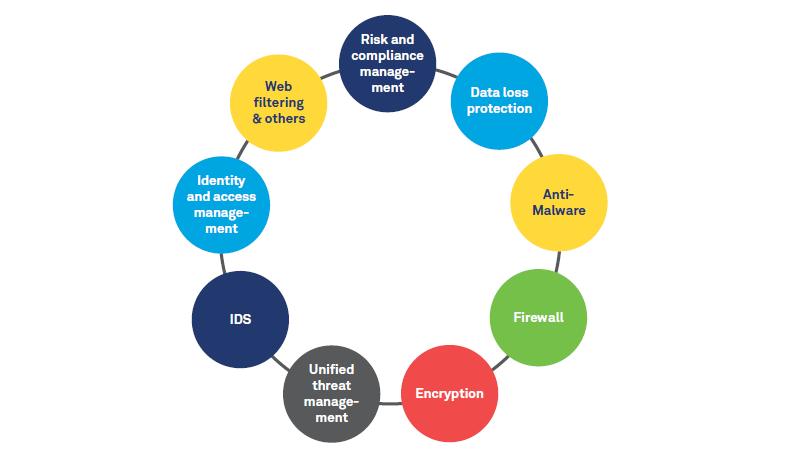
Figure 4: Cybersecurity Tools/ Solutions
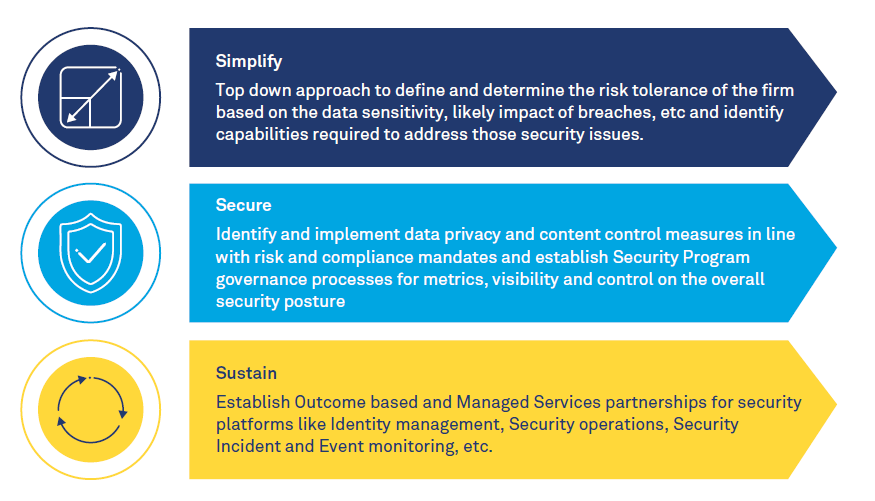
Figure 5: Integrated 3S Approach

Figure 6: Case in Point
Platform-based approach to manage cybersecurity
Managing cybersecurity in the digital age requires a vastly different blueprint to traditional methods of managing security. The imperative is to create a multi-disciplinary approach that combines risk and compliance, IT, and security capabilities and deliver platforms that address the broad security needs of an organization. The security platforms typically cover a gamut of solutions that span across core security domains, operations, audit/ review, and AI/ analytics. The advantage of the platform- based approach is the ability to bring deep specialization in each of these fundamental building blocks to cybersecurity along with the standardization and benchmarking of policies and procedures.
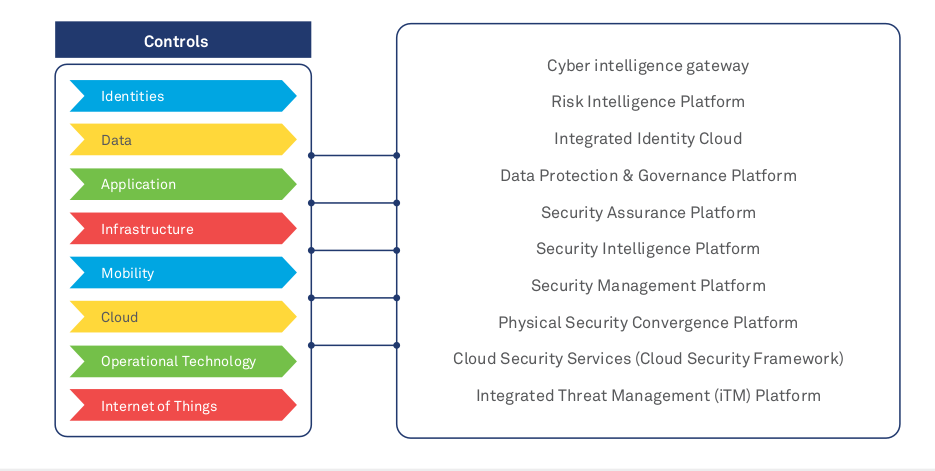
Figure 7: Case in Point
New ways of working to prevent cyber threats
Cyber threats are growing in frequency and severity, thereby making traditional approaches to security less effective. Along with increased focus on fundamental aspects like updating patch management and stronger third-party risk and compliance procedures, emerging technologies like Cloud, AI and ML, RPA, and Big Data can help orchestrate more effective cybersecurity strategies.
References
1 https://www.gartner.com/newsroom/id/3871063
2 https://www.csis.org/analysis/economic-impact-cybercrime
4 Forrester Top Cyber Security Threats in 2018
5 IBM Security and Ponemon Institute Cost of Data Breach Study 2018
Sakshi Agarwal
Pre-Sales Consultant, Financial Services Securities & Capital Markets, Wipro Limited.
Sakshi is working in Wipro as a Pre-Sales consultant for Securities and Capital Market clients across the Americas and Europe. She has completed her Master’s in Business Administration from IIM Udaipur, batch of 2016-18.