Exchange of Cyber Threat Intelligence Among Peers Using Decentralized Identity Networks and IoFT
The ability to exchange cyber threat intelligence (CTI) in privacy preserving and in a secure manner is vital for enterprises to manage their security risks effectively. Securing the CTI involves sanitizing privacy data from the identified threat information and dynamically generating Indicators of Fraudulent Transactions (IoFT) that will contain only the relevant CTI. The exchange is facilitated by usage of the decentralized identity network that permits participants on the network to establish trust with each other and avail secured communication channels to exchange information.
However, there are some inherent challenges:
An innovative solution to mitigate threats
IoFT are cyber threat intelligence metadata derived from the fraudulent behaviour pattern that is relevant for each domain. These fraudulent patterns are validated by respective domain experts. The IoFT will be devoid of any privacy information, but will have sufficient data elements to convey potential cyber threats as applicable for the respective domain. This offers greater confidence for peers to collaborate and address common cyber threats more effectively. In addition,
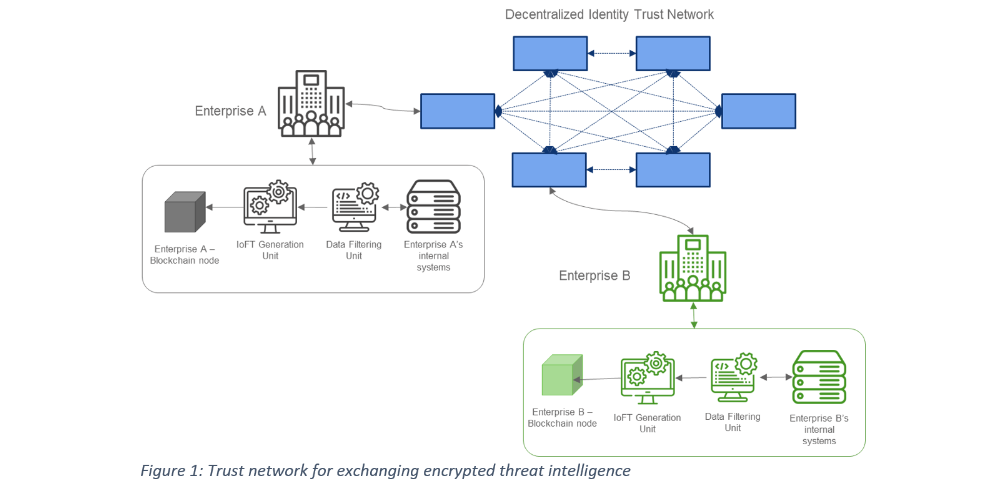
The infographic above depicts a trust network of financial Institutions. In the Figure Enterprise A & Enterprise B are financial institutions, both participants of the trust network. The Enterprises can leverage the decentralized Trust network to exchange CTI information using IoFT among the peer participants of the network. Enterprise A can exchange details of fraudulent transactions that it has identified with the peer organization Enterprise B in privacy preserving manner using IoFT. This would help Enterprise B to address similar fraudulent transactions more effectively, thereby preventing incurring financial losses by such transactions.
Here are a few use cases that demonstrate the applicability across various business domains:
Organizations can identify and weed out fraudulent transactions in the shortest possible time. Access to quality threat intel and diligent information sharing amongst peers can help minimize enterprise risk.With IoFT based solutions, organizations can now restrict what is being exchanged to actionable CTIs without exposing confidential information of the organization.
Industry :

Vinod Panicker
Global Head, Open Source , Blockchain and AI Security, Cybersecurity & Risk Services, Wipro
Vinod has over 22 years of experience in software development and product architecture. Vinod currently leads the open source , blockchain and AI security initiatives for the cybersecurity practice at Wipro. He is an expert in decentralized identity, blockchain security, building open source solutions, community-led tools development, open-source licensing, and re-engineering of products.

Sumod Rajan George, PMP
Sr. Project Manager, Cybersecurity and Risk services, Wipro
Sumod has over two decades of experience in software development, managing various projects and programs for business domains, such as retail, finance, healthcare, and transportation. He is currently part of the open source and blockchain security practice team with CRS, which focuses on security for open source and blockchain technology-based solutions.